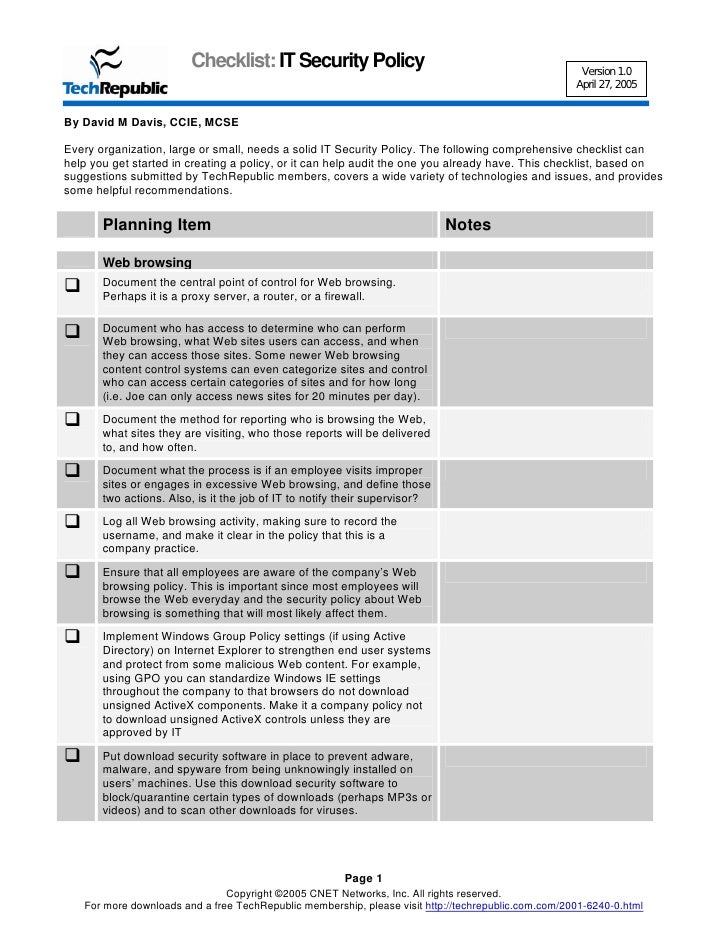
Iso Security Breach Template
In today’s business environment, protection of information assets is of paramount importance. It is vital for a..
SAMPLE TEMPLATE Massachusetts Written Information Security Plan Developed by: Jamy B. Erik Rexford Buchanan & Associates 33 Mount Vernon Street Boston, MA 02108 617-227-8410 www.buchananassociates.com jmadeja@buchananassociates.com Each business is required by Massachusetts law to evaluate security risks and solutions in. If notified of a privacy breach by a business area directly, open an incident request with the ITOC to activate the incident response plan for a suspected privacy breach. When notified by Information Security Office that the privacy breach Incident Response Plan has been activated, perform a preliminary analysis of the facts and assess the situation to determine the nature of incident. Oct 04, 2013 New ISO/IEC 27001 can help. Info: This news belongs to our archive. The revised version of the popular information security management system standard ISO/IEC 27001 is now available. The standard helps companies secure their information assets – vital in today's world where the number and sophistication of cyber-attacks is on the rise.
company to demonstrate and implement a strong information security framework in order to comply with regulatory requirements as well as to gain customers’ confidence. ISO 27001 is an international standard designed and formulated to help create a robust information security management system. It is a systematic approach to managing confidential or sensitive corporate information so that it remains secure (which means available, confidential and with its integrity intact).
ISO27001 explicitly requires risk assessment to be carried out before any controls are selected and implemented. Our risk assessment template for ISO 27001 is designed to help you in this task. Although specifics might differ from company to company, the overall goals of risk assessment that need to be met are essentially the same, and are as follows:
Risk assessment template for ISO 27001
- Identify risk.
- Determine if existing control measures are adequate as per company’s appetite for risk.
- Reduce the level of its risk by adding precautions or control measures, as necessary.
What is risk assessment?
To start from the basics, risk is the probability of occurrence of an incident that causes harm (in terms of the information security definition) to an informational asset (or the loss of the asset). In essence, riskis a measure of the extent to which an entity is threatened by a potential circumstance or event. It’s typically a function of the adverse impacts that would arise if the circumstance or event occurs, and the likelihood of occurrence.
Other risk assessment frameworks
The purpose of risk assessment is to identify:
- Threats to organizations (i.e., operations, assets, or individuals) or threats directed through organizations against other organizations or the nation.
- Vulnerabilities internal and external to organizations.
- Adverse impact to organizations that may occur given the potential for threats exploiting vulnerabilities.
- The likelihood that harm will occur.
The end result is determination of risk—that is, the degree and likelihood of harm occurring. Our risk assessment template provides a step-by-step approach to carrying out the risk assessment under ISO27001:
- Calculate the asset value.
- Identify vulnerability.
- Identify threats.
- Identify probability of threat and impact severity.
- Calculate risk score.
- Ascertain and establish controls.
Identify the assets and their value
Security Breach Policy Template
Identifying assets is the first step of risk assessment. Anything that has value and is important to the business is an asset. Software, hardware, documentation, company secrets, physical assets and people assets are all different types of assets and should be documented under their respective categories using the risk assessment template. To establish the value of an asset, use the following parameters:
- Cost of the actual asset.
- Cost to reproduce it.
- Cost if stolen.
- Value of intellectual property.
- Price others are willing to pay for the asset.
- Cost to protect the asset.
Security Breach News
Once this is done, map each asset to its confidentiality, integrity and availability (CIA) levels and arrive at a rating. Typically, the categories for asset value could be Very High, High, Low and Medium.
- Identify vulnerabilities
Vulnerabilities of the assets captured in the risk assessment should be listed. The vulnerabilities should be assigned values against the CIA values.
A vulnerability is the existence of a weakness, or error in design/implementation, that can lead to an unexpected, undesirable event compromising the security of the system, network, application, or process involved. The goal here is to identify vulnerabilities associated with each threat to produce a threat/vulnerability pair.
Vulnerabilities could be categorized as Very High, High, Low, and Medium.
- Identify threats
A threat is a potential event that may cause an unwanted, harmful incident. In the risk assessment template, threats are generally categorized under headings such as malicious activity, malfunction, people and environmental and then scored as Very High, High, Medium, or Low.
Identify probability and business impact of potential threats
More ISO 27001 stories
The next step using the risk assessment template for ISO 27001 is to quantify the probability and business impact of potential threats as follows:
- Frequency with which the threat could take advantage of the vulnerability.
- Productivity loss and cost.
- Extent and cost of physical damage that the threat could cause.
- Value lost if confidential information is leaked.
- Cost of recovering from a virus attack.
The impact severity is calculated as shown below
Impact severity = Asset value x threat severity x vulnerability severity
Determine the probability that a threat will exploit vulnerability. Probability of occurrence is based on a number of factors that include system architecture, system environment, information system access and existing controls; the presence, motivation, tenacity, strength and nature of the threat; the presence of vulnerabilities; and, the effectiveness of existing controls.
Calculate risk scoreHow to disable avast secure browser.
The risk score is calculated as follows
Risk Score = Impact severity x probability
The risk score may be depicted as below:
Iso Security Breach Template 2017
Risk Score | Description |
| Low | Accept |
| Medium | May need to add additional control |
| High | Need to treat |
| Very High | Requires immediate attention |
Risk treatment plan
After the risk assessment template is fleshed out, you need to identify countermeasures and solutions to minimize or eliminate potential damage from identified threats.
A security countermeasure must make good business sense, meaning that it must be cost-effective, with benefits outweighing the costs. This requires a cost/benefit analysis.

A commonly used cost/benefit calculation for a given safeguard is:
(ALE before implementing safeguard) – (ALE after implementing safeguard) – (annual cost of safeguard) = value of safeguard to the company.
Risk assessment template for ISO 27001
For example, suppose the Annualized Loss Expectancy (ALE) of the threat of a hacker bringing down a Web server is Rs 12,000 prior to implementing a suggested safeguard and Rs 3,000 after implementing the safeguard. If the annual cost of maintenance and operation of the safeguard is Rs 650, then the value of this safeguard to the company is Rs 8,350 each year.